by Business Analysis (BAPL).
What is authenticity? What is authentic? I once read a paper that described two different perspectives of authenticity. The first being how true is something to the social genre that the company or place wants to position itself in, and the second is how close does the company or products stay true to the core beliefs of the company itself. The paper used two pizza shops to describe authenticity. One pizza shop marketed itself as a hip place to be and was considered authentic in that it created truly original pizza’s that were representative of the social genre the shop represented, while the other made authenticity mean the pizzas were created from the true raw materials which represented the core beliefs of the shop so the shop remained authentic to these beliefs.
The definition of authentication in a computing sense is the process or action of verifying the identity of a user.
Another definition identifies authentication as the process or action of proving or showing something to be true, genuine or valid.
In IAM terms we can take authentic or authentication to mean verifying your identity, and the only way to do that is to validate that you are the person logging in by providing the right login credentials. These credentials tie in with the identity information provided when the account was initially provisioned or registered, which typically are the username and password combination, but that does not always have to be the case.
So, for us to actually verify our identity, we need to have identity information already in place to verify against. With this in mind, authentication is in fact a two-part process that
involves firstly provisioning the identity to the resource / application, and then using login credentials to verify the identity during login.
We have already discussed provisioning in an earlier blog. You might have forgotten about that one, I introduced the idea of provisioning through a quote from Mark Zuckerberg and then outlined my partners apprehension in creating a Facebook account because creating an account exposes identity information.
“At Facebook, we build tools to help people connect with the people they want and share what they want, and by doing this we are extending people’s capacity to build and maintain relationships.”
It’s all very well to create an account, but how can we have the confidence that our details are to be held securely? Or in fact, how can we be sure that the person creating the account is truly who they say they are. How do we validate the identity? During the provisioning process, we prove that the identity is valid through the HR department. This might involve confirming our identity with 100 points of identity proof like a passport, drivers’ licence or credit cards. Online sites are available that can validate identity information and provide the identity proof. The main one I am familiar with is run by Australia Post. You can access it at http://australiapost.com.au and verify identity information here.
As mentioned, in a corporate environment the persons details are typically captured by HR and the identity proof documents are usually sighted and copied as part of the onboarding process. It then results in the HR system becoming the trusted source of truth for identity information.
Once we have confidence of the identity through proof of identity documents, the next step is to ensure that the person authenticating is the right person and not a usurper of the person’s identity and we do this through the login process.
The basic login to a computer is quite straight forward. Using the username and password provided, the computer login process compares these two credentials by looking up the username and comparing the password hash given with the password hash saved against the username. A successful compare results in a successful login.
The following sequence diagram follows the process for login to a cloud-based application using single sign on (SAML (Security Assertion Mark-up Language)). This login process requires validation of the credentials (whether a username / password combination or other factor) against the credentials held in the identity provider database, (in this case Azure AD).
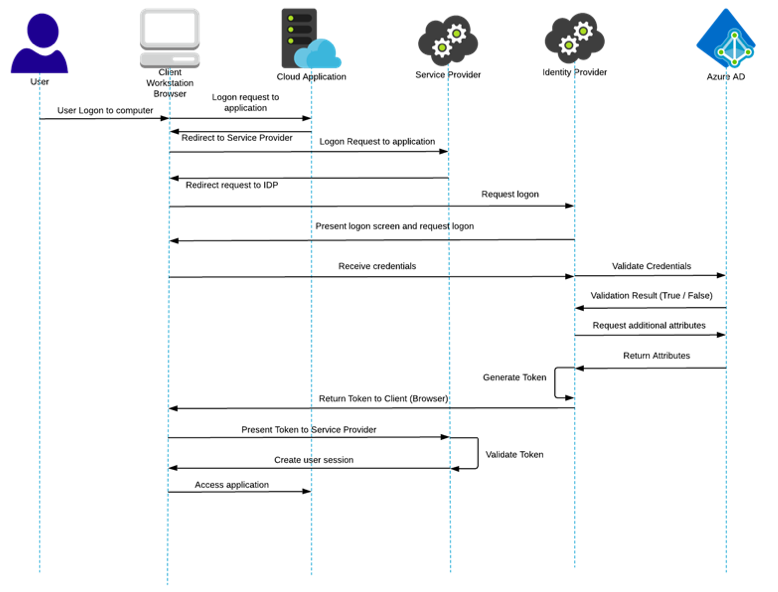
Now let’s extend this because Single Sign On (SSO) uses these successful credentials to create a token that is used to authenticate to SSO enabled applications. By creating an encrypted token, the login credentials remain secure and the application receives verification of the user’s identity. In addition, the token can be used to carry additional identity data such as group information that may be used to provide specific profile authorisation.
It gets quite messy and I don’t think delving any further into the labyrinthian area of authentication is going to make us any the wiser. Suffice to say, that once we have successfully authenticated, we can use this same token to permit login to other applications and hence establish a Single Sign On process. There are loads of online diagrams describing the login process for single sign on using SAML (the one above is taken from the ping identity online documentation at http://www.pingidentity.com ).
Of course, there are three different methods we can use to verify our identity. These are:
- Something you know (like a username or password)
- Something you have (Like a USB stick or mobile phone)
- Something you are (like a face scan, fingerprint or other biometric)
Multi factor authentication uses two or all three of these in combination while two factor authentication uses two separate factors.
E.g.: Two factor would use something you know + something you have, multi factor may use a combination of something you know + something you have and maybe another thing you know or have or are.
Needless to say, the better methods move away from passwords and even remove usernames to login. Authentication is moving quite rapidly to find better, simpler and more secure ways to login. The Fido Alliance is a group of organisations that are working towards these ideals. To date they have provided simple, secure login and are now working with vendors to implement these into solutions.
If you want more information on this check out the fido alliance website.
If we believe that an authentic pizza is one that is true to the recipe and the ingredients, then we can consider these pizza’s as individual as we are. Our identity is comprised of the attributes that make us individuals and we prove our authenticity through the login process.
Login: the act of verifying our identity and ensuring that identity is authentic. Maybe we aren’t as real as pizza, perhaps we fail the authenticity test (otherwise known as a failed login), or maybe we are as real and those ingredients that makes us individuals (our attributes) allow us to prove our authenticity through the login process, either something we know, something we may be, or something we have. More authentic than pizza? Sacrilege.
