by Business Analysis (BAPL).
“At Facebook, we build tools to help people connect with the people they want and share what they want, and by doing this we are extending people’s capacity to build and maintain relationships.”
In the first part of this series we talked about how my partner has lacked the confidence to re-enable her Facebook account. For her, Facebook became a scary beast that allowed others to stalk and peruse her personal life. There were few if any controls to allow her to restrict the access for unknown people and provide the security that she needed to have to use the application. This is still the case by the way, although Mark Zuckerberg seems to think otherwise in the quote we have cited at the head of this entry. But the quote does provide a great segue into what this blog entry wants to cover. In this entry I want to move on from the initial account registration to start managing the identity and the identity lifecycle.
This becomes the core of identity management with individual components such as the identity vault and integration connections providing the means to capture, consolidate and distribute / provision accounts across the company’s IT landscape.
We have said this before, but I will say it again. Gartner defines Identity Management as the set of processes required to provide the right access for the right people to the right applications at the right time and for the right reasons. The Identity Lifecycle takes this from cradle to grave. We don’t see too many digital identities entering the grave, and we have already covered off in our previous blog entry how the stork delivers the new identity. This blog will take us through the identity lifecycle journey with the aim of identifying the core processes involved in setting up an identity management system to introduce, manage and remove an identity within an organisations environment.
Let’s put this into context. The two following diagrams provide high level views of the IAM processes and integration.
The primary processes of the Identity lifecycle include:
- Provisioning
- Changes / Updates
- De-provisioning
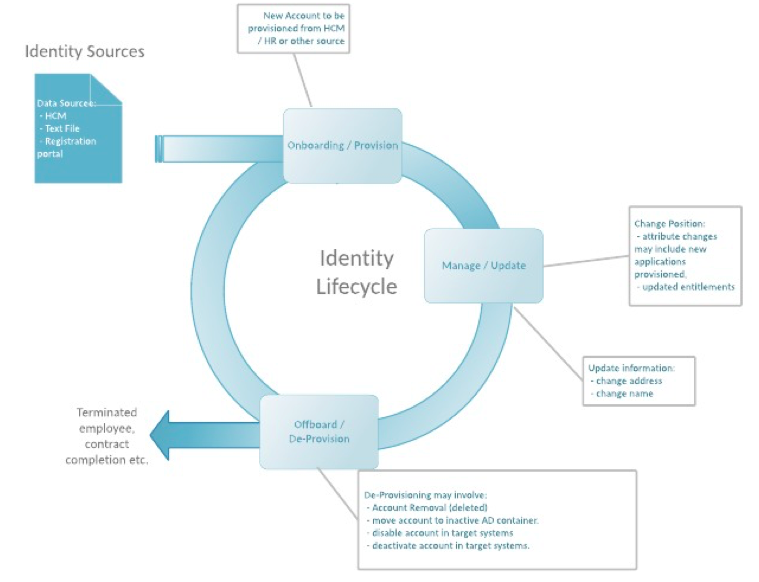
Figure 1 – Identity Lifecycle Processes
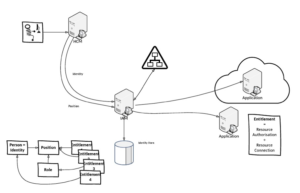
Figure 2 – Identity Integration Context Diagram
This simple diagram shows:
- The Source of Truth (SoT)
- The Identity Vault (Vault)
- The Active Directory (target)
- A cloud and on-premise application.
For the record I have added in how we can assign access based on attributes, position or roles. Each application or target system is considered an entitlement, although an application may have multiple entitlements with each one having a different level of access for a user to operate at different profile levels.
Traditional methods of achieving this were performed manually. The IT Service Desk would usually be requested to create, modify or remove an account for a staff member, visitor or other identity type (which I put into a general label of Person of interest or POI).
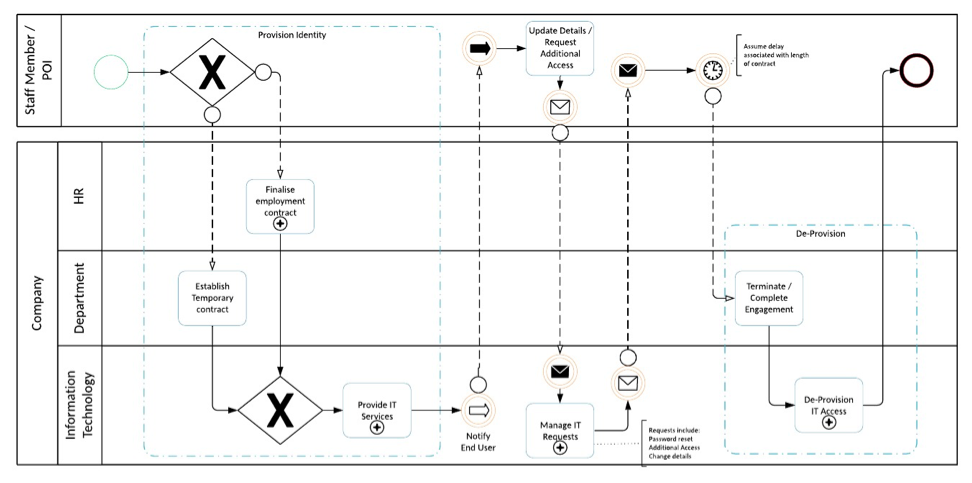
Figure 3 – Identity Lifecycle BPMN High Level Process
There are a few key aspects of identity management that are needed to make the lifecycle management processes work. The process map above outlines at a high level the Identity lifecycle journey.
It starts with the Source of Truth or Authoritative Source for the identity. Typically, this might be the HR or HCM (Human Capital Management system, the registration system which might be extended to allow updates to an identity, or some other system that has the ultimate truth with respect to the identity attributes. IAM synchronises identity data from an authoritative source to each connected / provisioned application. Provisioning involves a number of steps.
Firstly, the identity information is consolidated from the source of truth to the identity vault. The vault stores all identity information for the individual. This is where the person becomes is represented as a digital identity.
Secondly, whether the identity should be provisioned to the application is determined by the IAM system based on specific preconfigured business rules that assess the attributes of the identity such as position, location and/or department against a prescribed set of requirements.
Thirdly, once the IAM system has determined that the identity is to be provisioned to the application, a subset of the identity data from the vault is used to automatically create the account and assign specific access rights to the application for the identity.
The following process diagram outlines these steps to provision an account to an entitlement.
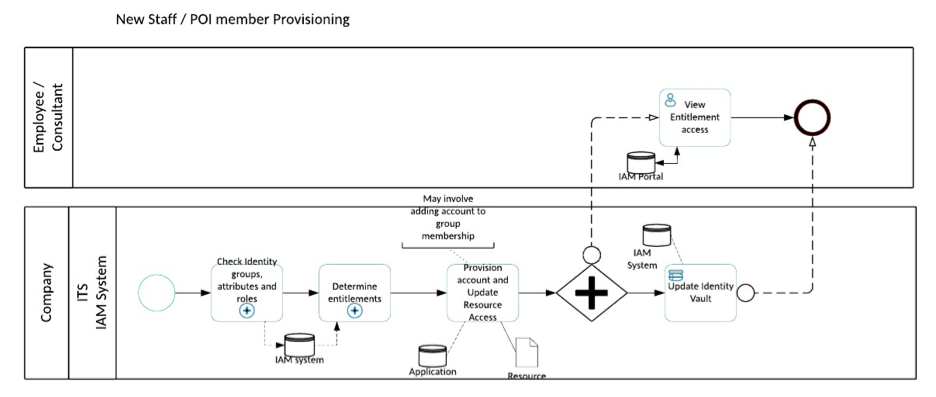
Figure 4 – Identity Provisioning
But people are not static entities. They may change their name, address, phone number, position, location or department or any one of a large number of attributes that define us as individuals in a corporate environment. Managing the Identity Lifecycle involves ensuring these changes are replicated from the Source of Truth to all target systems. Despite what people might think, Active Directory is NOT the authority on personal identity data. To change identity information, we need to change the data in the Source of Truth for the identity. IAM will synchronise the attributes changed to each connected system the identity is provisioned to, overwriting any data that is in each application for the identity attribute being changed.
By way of example, I could use a hypothetical situation where my daughter might find a partner that she wants to be with and, after the appropriate courting period, they agree to be wed.
At a digital level this simply changes a few attributes such as last name and title. These would be modified at the source of truth and synchronised via the IAM system to the vault and downstream applications.
This may seem a little impersonal, but it could be argued that IAM provides greater personal control over your information than has previously been allowed.
Ultimately, we move on to the termination. Rarely do we need to remove all traces of an identity from our systems. IAM provides much greater security in a more-timely manner than would otherwise be available through manual or semi-automated processes. In IAM terms, we consider that the terminated identity “will be back”. Perhaps they will return as a client or visiting consultant, or perhaps as a staff member in a different position. In any case, most IAM systems will disable accounts in the target systems but will retain the identity information in the identity vault and the source systems.
IAM automates the provisioning, change and de-provisioning processes. Business rules dictate what access is provided on which the IAM system acts and ensures that each provisioned application is provided only what data is required to enable the right access for the individual.
Facebook may be providing the tools that enable people to connect with others, but this is a limited version of what IAM provides in an organisation. Within the company’s environment IAM ensures that security of company and personal identity data is maintained, access is provided to data and applications across the organisation and the relationship that is required between people, applications and resources is established and maintained automatically by simple changes to our personal data.
Identity Management is extending far beyond the boundary of the organisation. Today we can use Facebook accounts to login to online and corporate sites, but what if we could turn that around and control our own identity data to permit parts of it to be consumed in creating accounts in Facebook, Google, Yahoo and other corporate and online sites.
I think at that point even my partner might be happy to venture into the sphere of the internet again.
