by Business Analysis (BAPL).
When my youngest daughter Tams turned 18, she was ready to hit the clubs in the city. This had been a long time coming and she wasn’t going to miss what had become a rite of passage when the opportunity presented itself. On the night of her birthday she presented herself to the well-known clubs in the valley. Needless to say, as a father I had to hold my tongue and pray that she made it home without too much trouble. She was well aware that she would need some ID showing her age to allow her to enter the pubs and bars of the streets. But Queensland had created the lockout laws only the previous year introducing strict new rules with regards to patrons accessing the popular clubs with the intent of reducing alcohol induced crime in the areas. Clubs were now required to bar entry after 1 am and alcohol was to be served only until 3am.
Turning 18 had provided Tams the right to access the clubs. This entitlement was granted automatically when she turned 18 and had been the case for as long as we can remember. However, the lockout laws highlight the privilege that this entitlement provides to us and one that we have to date taken for granted.
In Identity Management terms, the definition of an entitlement is: “the amount to which a person has a right.” Google Dictionary (2020). The example I provide here indicates that the general public in Brisbane at least have a right to access the clubs so long as they can prove they are over 18 years of age, but that there are constraints to this right introduced by legislation that will restrict the rights we have
In this blog, I want to introduce entitlements, granting a user an entitlement through a request for access and authorisation within an entitlement.
As with the entitlement granted to 18-year olds access to clubs in Brisbane, in organisations where an Identity and Access Management system exists, entitlements may be granted automatically based on specific attributes of the identity.
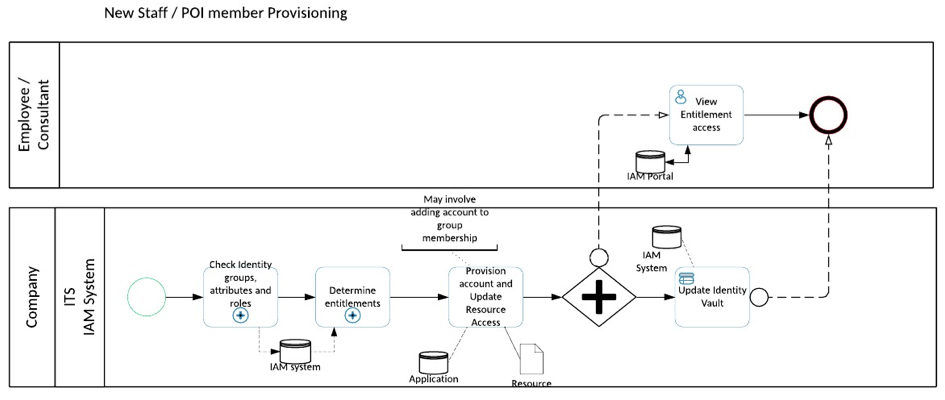
If we look at a process mapping the assignment of the entitlement to enter the clubs at 18 we have something not too different from the process above. We just identify the age as one of the attributes checked and permit access based on that attribute.
Access and authorisation are terms often considered the same thing and used interchangeably. But these are different features in Identity and Access Management. In each case they provide access for the identity to an entitlement, however while an identity may have access to a resource, they may not have the authorisation to access all the data or application that the resource hosts. As an example, a user may have access to a file server or cloud storage. But the ACL’s dictate what authorisation the user has access to on that data store.
Business policies and business rules define what access and authorisation is provided to the identity automatically.
In the event that the user / identity requires access to an additional resource, or that a higher level of authorisation is required, the identity will typically request access to the resource / application with the required authorisation level. This entitlement request requires approval before being assigned. In this particular instance approval is required from two separate approvers.

The following use case supports this access request process.
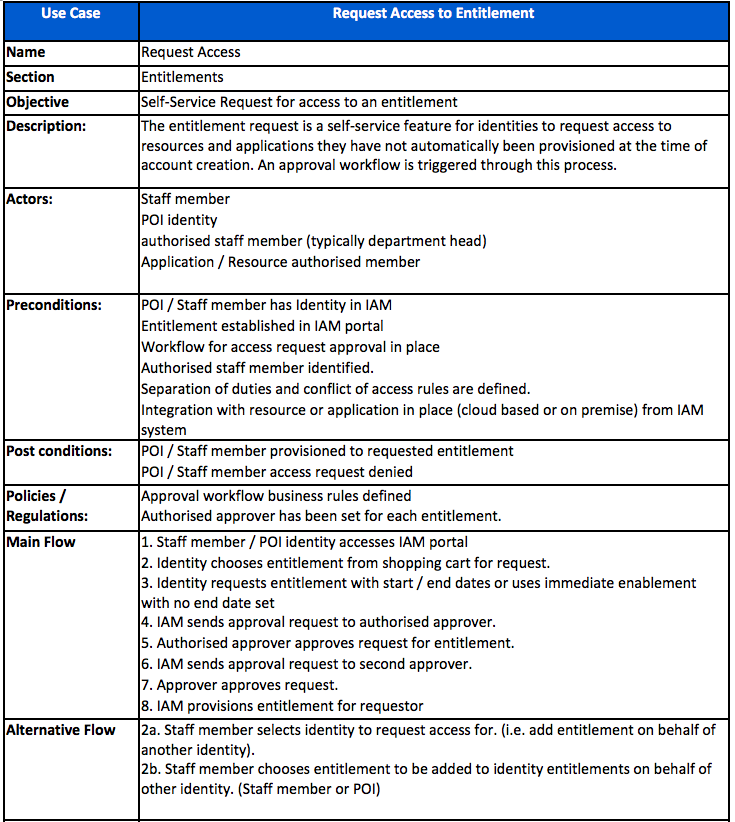
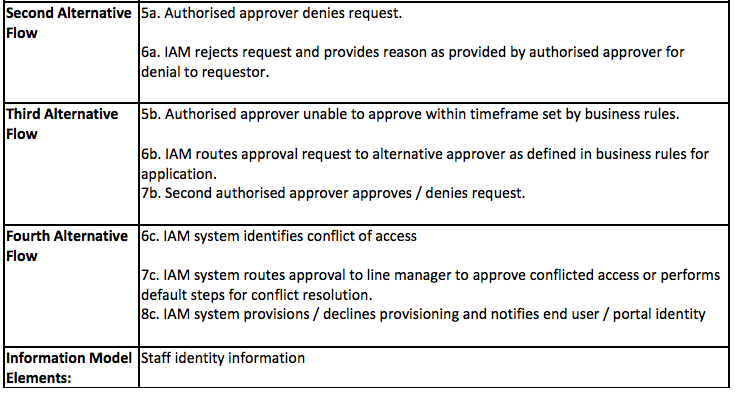
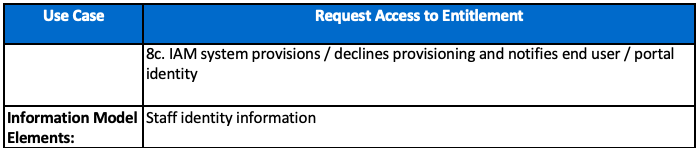
The process may be as simple as that pictured, or as complex as is portrayed in the Use Case. Needless to say, the functional and non-functional requirements will include levels of self-service capability, workflow development, triggers to re-route requests, assign approvers and send notifications.
Providing access to a resource or application is a business decision. The questions of who, why, when and what access is provided are largely determined by the business and implemented as rules within the IAM system to automatically assign the entitlement to the identity, just as the entitlement to access the clubs and bars of Brisbane are automatically given once specific determinants are fulfilled and in compliance with the laws of the State. In this case the age has exceeded 18 years.
Fortunately, IAM systems can use a broad set of attributes to determine access, but none of these relate to our human side while security staff need to make the decision on proof of age.
Like with the rest of us, this won’t last too long. 😉
